Cybersecurity is a critical aspect of modern business and personal data protection. With the increasing complexity and frequency of cyber threats, staying informed and implementing robust security measures are essential for safeguarding digital assets.

Cyber Security
Protecting Systems & Networks
Cybersecurity involves protecting systems, networks, and programs from digital attacks. These attacks are typically aimed at accessing, changing, or destroying sensitive information, extorting money from users, or interrupting normal business processes.
Cyber Security
Types of Cybersecurity Threats
Malware
Malicious software like viruses, worms, ransomware, and spyware that infiltrates systems and causes damage.
Denial-of-Service (DoS) Attacks
Flooding a network or server with traffic to overwhelm resources and render it inoperable.
Phishing
Fraudulent attempts to obtain sensitive information by disguising as a trustworthy entity in electronic communications.
SQL Injection
Inserting malicious code into a server that uses SQL, which forces the server to reveal protected information.
Man-in-the-Middle (MitM) Attacks
Eavesdropping attacks where the attacker intercepts and relays messages between two parties.
Zero-Day Exploits
Attacks on vulnerabilities in software that are unknown to the software creator or not yet patched.
Cyber Security

Key Cybersecurity Practices
Regular Updates and Patching: Ensuring all software and systems are up-to-date with the latest security patches.
Firewalls and Antivirus Software: Implementing firewalls to monitor and control incoming and outgoing network traffic and antivirus software to detect and eliminate malicious software.
Encryption: Protecting data by converting it into a code to prevent unauthorized access.
Strong Passwords and Multi-Factor Authentication (MFA): Using complex passwords and adding an extra layer of security through MFA.
Security Awareness Training: Educating employees about cybersecurity risks and safe practices.
Incident Response Planning: Preparing and testing a plan for responding to cybersecurity incidents to minimize damage.
Featured Case
We Focused on Results
Web & Marketing
Our mission is to aid our clients in bestowing a professional front to the ma
Website Design
html, css, javascript, bootstrap, Graphic design, W3C standards
Website Development
php, wordpress, hosting
Search Engine Optimization
google, google ads, marketing

CCTV Cameras
Provide the home health care programs at flexible schedules and cost-friendly
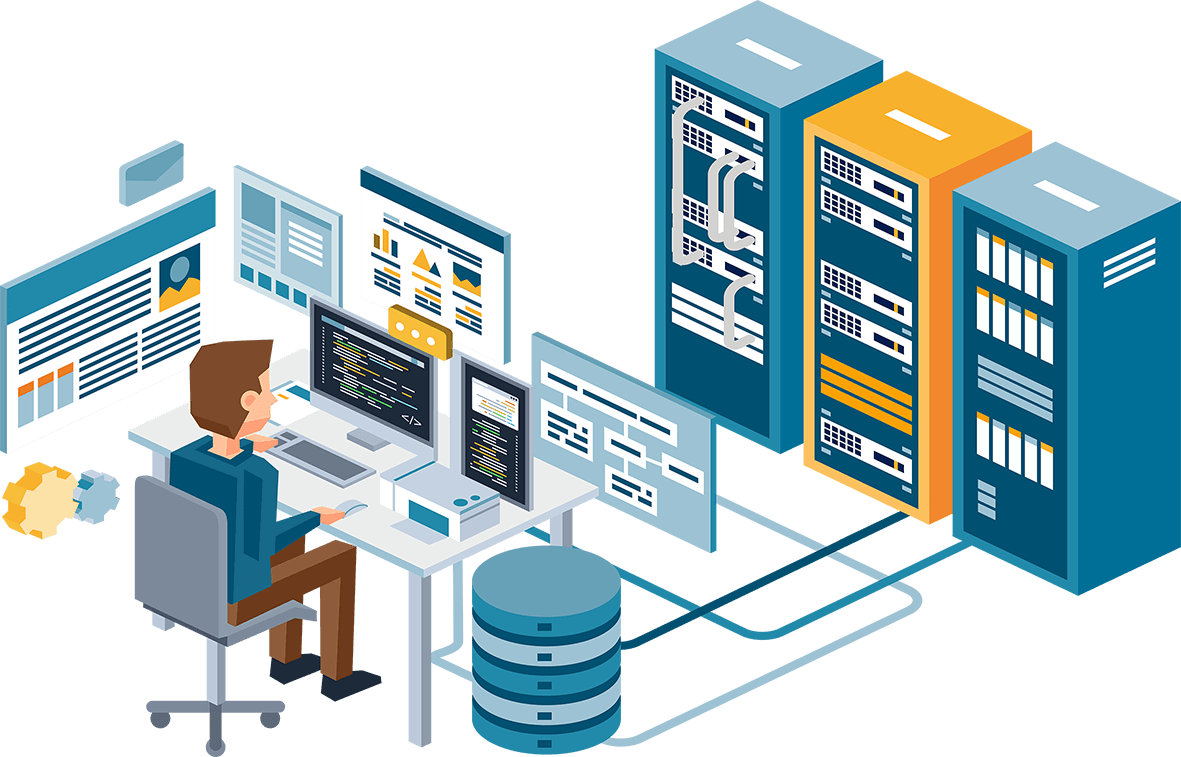
IT Infrastructure
IT infrastructure services encompass the design, implementation, management,
Network Infrastructure
LAN, WAN, and Wi-Fi
Server Management
Physical and virtual servers
Data Center Services
Storage

Telecommunications
A Photoshop template file to help you create realistic foil balloon words
Landline Telephone Systems
Voice communication
Switching Systems
Networking Equipment

Access Control System
Provided responsive customer support and fast turnaround on a modern.
Authentication
fingerprint, iris scan, facial recognition
Reader Devices
biometric scanners
Monitoring and Logging
real-time access



 AMC / Tech Service
AMC / Tech Service IT Infrastructure
IT Infrastructure Telecommunication
Telecommunication Surveillance CCTV
Surveillance CCTV Access Control
Access Control Web & Marketing
Web & Marketing